How To Background A Meterpreter Session
Manage Meterpreter and Trounce Sessions
Later on you successfully exploit a host, either a beat or Meterpreter session is opened. By default, Metasploit attempts to deliver a Meterpreter payload. A Meterpreter payload is uploaded to a remote machine that allows you to run Metasploit modules. If Metasploit is unable to deliver a Meterpreter payload so information technology opens a shell.
Depending on the module used to create a session, either a Shell or both a Beat out and Meterpreter session volition exist opened. This is because shell payloads are created by running a control on a remote machine, and they can exist easier to "launch". Some exploits are limited in functionality ,and vanquish commands crave less manipulation by the exploit.
A Meterpreter shell gives y'all admission to Metasploit modules and other deportment non available in the control beat.
A shell session opens a standard terminal on the target host, giving you similar functions to a terminal on your OS. The functionality can differ depending on the type of exploit used. Using a beat out does not provide the aforementioned deportment equally a Meterpreter shell.
Command Shell
"Command Vanquish" is listed under Beat out and Meterpreter. While the name is the same, the functionality is not. Meterpreter > Command Trounce will open a Meterpreter shell, while Vanquish > Command Vanquish will open up a standard terminal.
Manage Your Meterpreter Session
To access the session pages in the top bill of fare get to "Sessions".
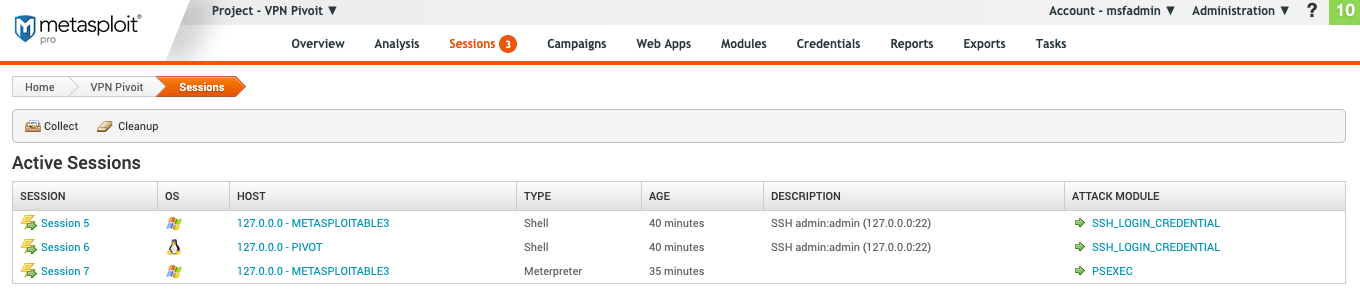
The Meterpreter "Active Sessions" page provides you lot with the following data:
- Session - The number of the session. These are attached to the session in sequential order of being created.
- Bone - The host operating system.
- Host - The host address and name.
- Type - The blazon of shell.
- Age - The time the session has been opened in minutes or seconds. Once 60 seconds is reached, fourth dimension is tracked in minutes.
- Description - Whatever data related to how the session was opened if available. For example, bruteforce opened sessions volition incorporate the username and countersign used.
- Attack Module - The exploit used to open the session.
View Available Meterpreter Actions
To run across all the available actions for a Meterpreter shell during a session, do the post-obit:
- Nether "Active Sessions" select a session that has a "Blazon" of "Meterpreter".

- On the session page, review the available deportment. From this folio, yous tin can launch a terminal, encounter available modules and run mail-exploitation actions.
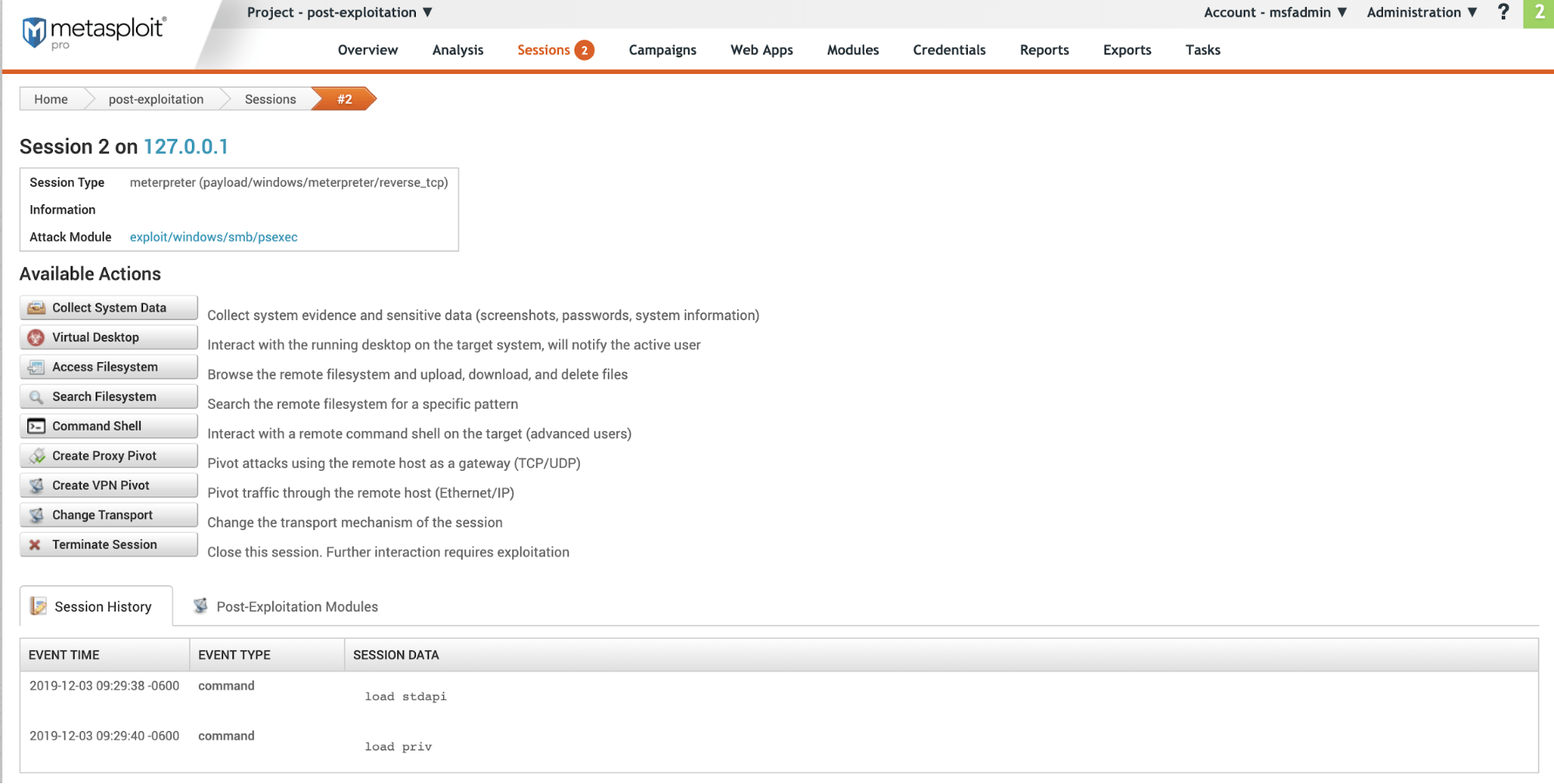
The Meterpreter session page has the following data:
- Session - Session number and target host accost. In the image above this is
Session 2 on 127.0.0.i - Session Type - The blazon of payload and module used to open up the session.
- Data - Any data on how the session was opened. If this was the effect of a bruteforce assault it will include the authentication blazon and credential pair used.
- Set on Module - Exploit used to open the session.
- Available Actions - All the available deportment that can exist taken.
- Session History - A detailed list of all actions taken during an open session.
- Post-Exploitation Modules - Modules available to run based on the Os and payload type.
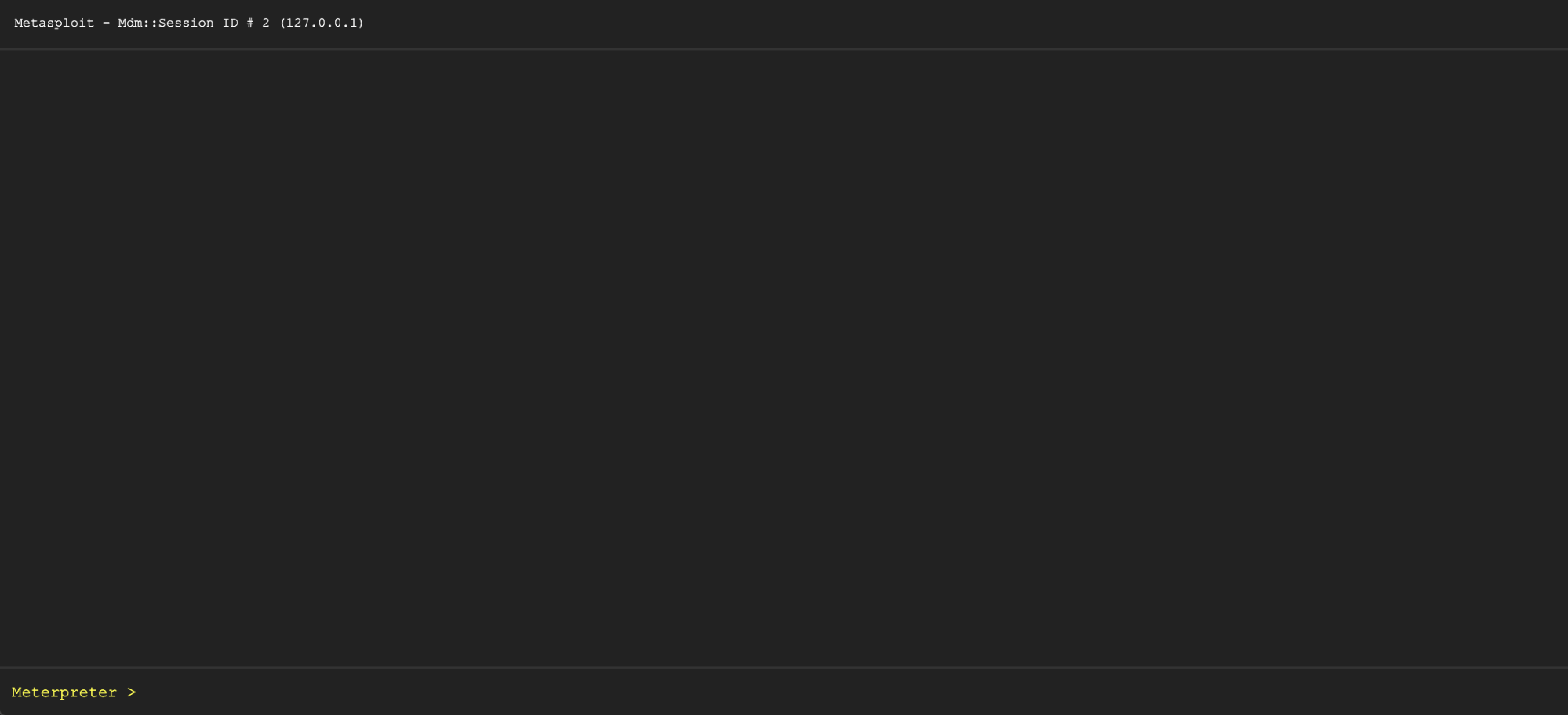
Launch the Meterpreter Control Shell
Under "Bachelor Actions" click Command Shell. It will open a blank terminal. At the height is the session ID and the target host address. In this example, the session ID is : Metasploit - Mdm::Session ID # 2 (127.0.0.1)
At the bottom is the shell input. Meterpreter >
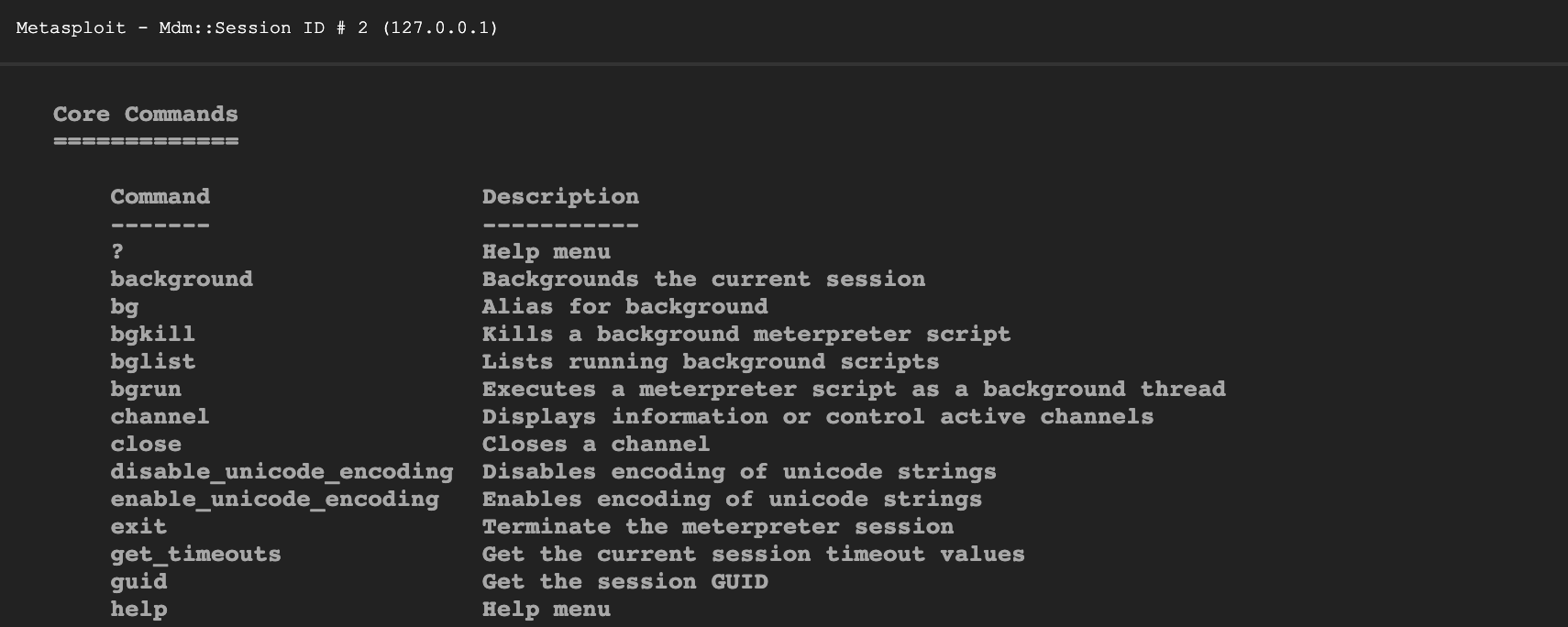
View Bachelor Meterpreter Beat Commands
-
To see a listing of available commands type
?.Meterpreter > ?It will display a list of bachelor commands with a description of each. From here you can run a module, review the target hosts files and get networking information. -
To shut down a session from the vanquish employ
quit.
Meterpreter Trounce Commands
ane
Cadre Commands
ii
=============
three
iv
Command Description
v
------- -----------
6
? Assistance menu
7
background Backgrounds the current session
8
bg Alias for groundwork
nine
bgkill Kills a background meterpreter script
ten
bglist Lists running background scripts
11
bgrun Executes a meterpreter script every bit a background thread
12
channel Displays information or control active channels
13
close Closes a channel
14
disable_unicode_encoding Disables encoding of unicode strings
xv
enable_unicode_encoding Enables encoding of unicode strings
16
leave Terminate the meterpreter session
17
get_timeouts Get the current session timeout values
18
guid Get the session GUID
xix
help Help menu
20
info Displays data virtually a Mail service module
21
irb Open an interactive Carmine shell on the current session
22
load Load i or more than meterpreter extensions
23
machine_id Get the MSF ID of the machine attached to the session
24
drift Migrate the server to some other process
25
pivot Manage pivot listeners
26
pry Open the Pry debugger on the current session
27
quit Stop the meterpreter session
28
read Reads information from a aqueduct
29
resource Run the commands stored in a file
30
run Executes a meterpreter script or Post module
31
secure (Re)Negotiate TLV packet encryption on the session
32
sessions Apace switch to another session
33
set_timeouts Gear up the current session timeout values
34
sleep Forcefulness Meterpreter to go placidity, then re-found session.
35
ship Change the current transport machinery
36
apply Deprecated alias for "load"
37
uuid Get the UUID for the current session
38
write Writes data to a channel
39
40
41
Stdapi: File organization Commands
42
============================
43
44
Command Description
45
------- -----------
46
cat Read the contents of a file to the screen
47
cd Change directory
48
checksum Think the checksum of a file
49
cp Copy source to destination
50
dir List files (alias for ls)
51
download Download a file or directory
52
edit Edit a file
53
getlwd Print local working directory
54
getwd Print working directory
55
lcd Change local working directory
56
lls Listing local files
57
lpwd Print local working directory
58
ls List files
59
mkdir Brand directory
60
mv Move source to destination
61
pwd Print working directory
62
rm Delete the specified file
63
rmdir Remove directory
64
search Search for files
65
show_mount List all mountain points/logical drives
66
upload Upload a file or directory
67
68
69
Stdapi: Networking Commands
lxx
===========================
71
72
Command Description
73
------- -----------
74
arp Display the host ARP cache
75
getproxy Display the electric current proxy configuration
76
ifconfig Display interfaces
77
ipconfig Display interfaces
78
netstat Brandish the network connections
79
portfwd Forward a local port to a remote service
80
resolve Resolve a gear up of host names on the target
81
route View and modify the routing table
82
83
84
Stdapi: System Commands
85
=======================
86
87
Command Description
88
------- -----------
89
clearev Clear the event log
90
drop_token Relinquishes any agile impersonation token.
91
execute Execute a command
92
getenv Become one or more surroundings variable values
93
getpid Get the electric current process identifier
94
getprivs Attempt to enable all privileges bachelor to the current process
95
getsid Get the SID of the user that the server is running as
96
getuid Go the user that the server is running as
97
kill Terminate a process
98
localtime Displays the target organisation's local date and time
99
pgrep Filter processes past proper noun
100
pkill Terminate processes by name
101
ps List running processes
102
reboot Reboots the remote computer
103
reg Modify and interact with the remote registry
104
rev2self Calls RevertToSelf() on the remote machine
105
vanquish Drop into a arrangement control vanquish
106
shutdown Shuts down the remote computer
107
steal_token Attempts to steal an impersonation token from the target process
108
suspend Suspends or resumes a list of processes
109
sysinfo Gets data nigh the remote system, such as OS
110
111
112
Stdapi: User interface Commands
113
===============================
114
115
Command Clarification
116
------- -----------
117
enumdesktops Listing all accessible desktops and window stations
118
getdesktop Get the electric current meterpreter desktop
119
idletime Returns the number of seconds the remote user has been idle
120
keyboard_send Send keystrokes
121
keyevent Ship key events
122
keyscan_dump Dump the keystroke buffer
123
keyscan_start Start capturing keystrokes
124
keyscan_stop Stop capturing keystrokes
125
mouse Transport mouse events
126
screenshare Sentry the remote user'south desktop in real fourth dimension
127
screenshot Catch a screenshot of the interactive desktop
128
setdesktop Modify the meterpreters electric current desktop
129
uictl Control some of the user interface components
130
131
132
Stdapi: Webcam Commands
133
=======================
134
135
Command Description
136
------- -----------
137
record_mic Tape audio from the default microphone for X seconds
138
webcam_chat Start a video chat
139
webcam_list Listing webcams
140
webcam_snap Accept a snapshot from the specified webcam
141
webcam_stream Play a video stream from the specified webcam
142
143
144
Stdapi: Audio Output Commands
145
=============================
146
147
Command Description
148
------- -----------
149
play play an sound file on target system, nothing written on deejay
150
151
152
Priv: Elevate Commands
153
======================
154
155
Command Description
156
------- -----------
157
getsystem Endeavor to elevate your privilege to that of local system.
158
159
160
Priv: Password database Commands
161
================================
162
163
Command Description
164
------- -----------
165
hashdump Dumps the contents of the SAM database
166
167
168
Priv: Timestomp Commands
169
========================
170
171
Command Description
172
------- -----------
173
timestomp Manipulate file MACE attributes
Manage your Vanquish Session
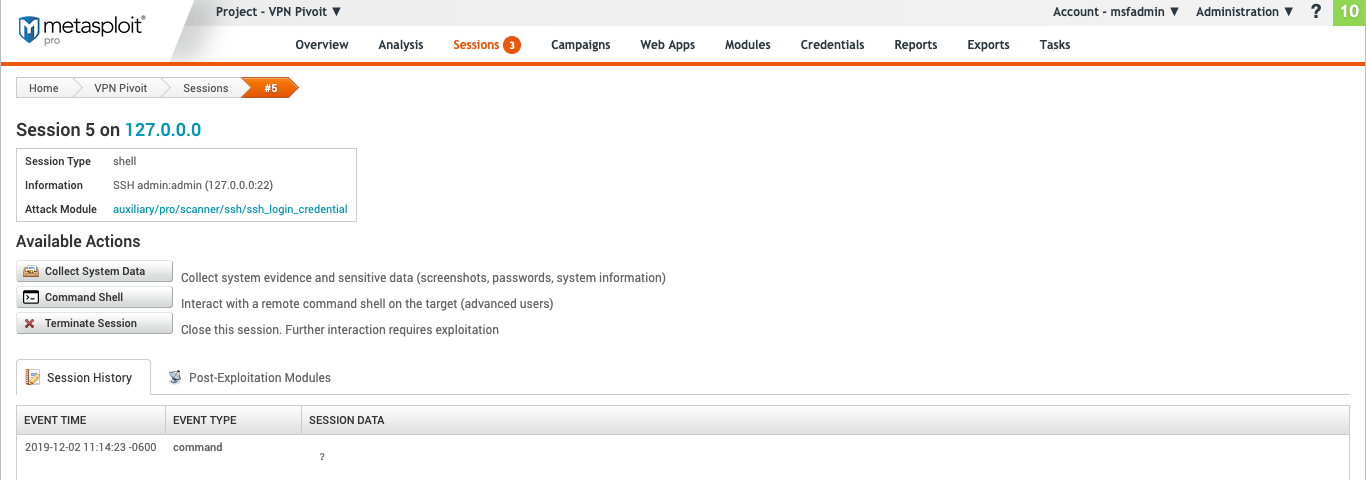
The Shell session page provides you with the following information:
- **Session - **Session number and target host address. In the image above this is
Session 2 on 127.0.0.i - **Session Type - **The type of payload and module used to open the session.
- Information - Any information on how the session was opened. If this was the result of a bruteforce attack information technology volition include the hallmark blazon and credential pair used.
- Assail Module - Exploit used to open the session.
- **Available Actions - **All the available actions that can exist taken.
- **Session History - **A detailed list of all actions taken during an open session.
- **Postal service-Exploitation Modules - **Modules bachelor to run based on the OS and payload blazon.
View Available Shell Actions
- Under "Active Session" select a session that has a "Blazon" of "Crush".

- Review the shell session page. From this folio, you can launch a shell and run post-exploitation actions. Since this is a shell session, the available "Mail-Exploitation Modules" will non be the same as a Meterpreter session. They volition depend on the exploit used.
The Shell session page has the following information:
- **Session - **Session number and target host address. In the image above this is
Session 2 on 127.0.0.1 - **Session Blazon - **The type of payload and module used to open the session.
- Information - Whatever information on how the session was opened. If this was the result of a bruteforce assail it will include the authentication type and credential pair used.
- Assail Module - Exploit used to open the session.
- **Bachelor Deportment - **All the available deportment that can be taken.
- **Session History - **A detailed list of all deportment taken during an open session.
- **Post-Exploitation Modules - **Modules available to run based on the Os and payload type.
Launch a Command Shell
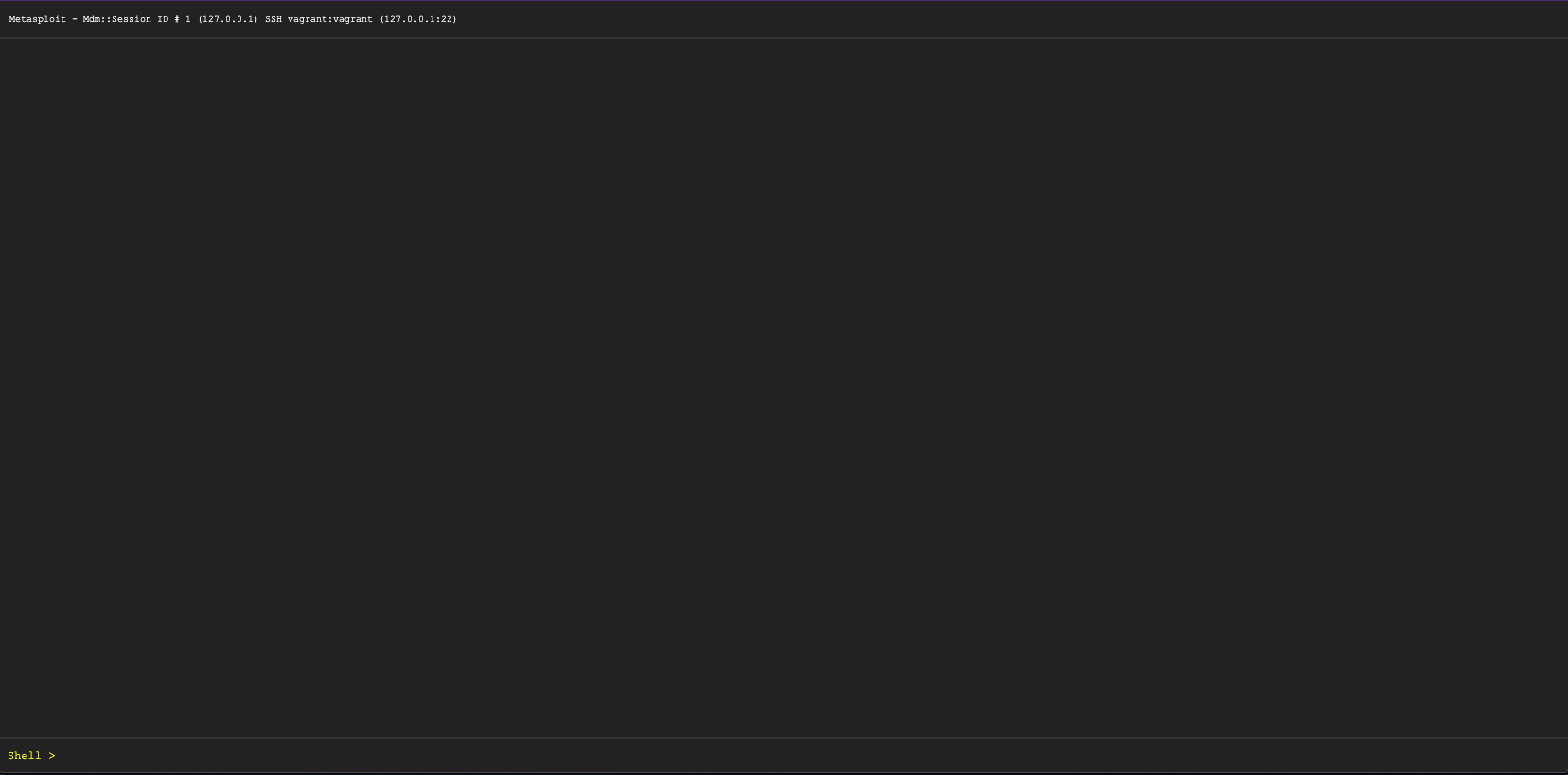
Under "Available Actions" click Command Trounce. It will and then open a bare final.
The session ID and the target host address are displayed at the pinnacle of the command shell. In this example, the session ID is : Metasploit - Mdm::Session ID # 1 (127.0.0.1) SSH vagrant:vagrant (127.0.0.1:22)
At the bottom is the shell input. Trounce > The commands available for the beat out will depend on the target host Bone.
How To Background A Meterpreter Session,
Source: https://docs.rapid7.com/metasploit/manage-meterpreter-and-shell-sessions/
Posted by: mclarenquity1983.blogspot.com


0 Response to "How To Background A Meterpreter Session"
Post a Comment